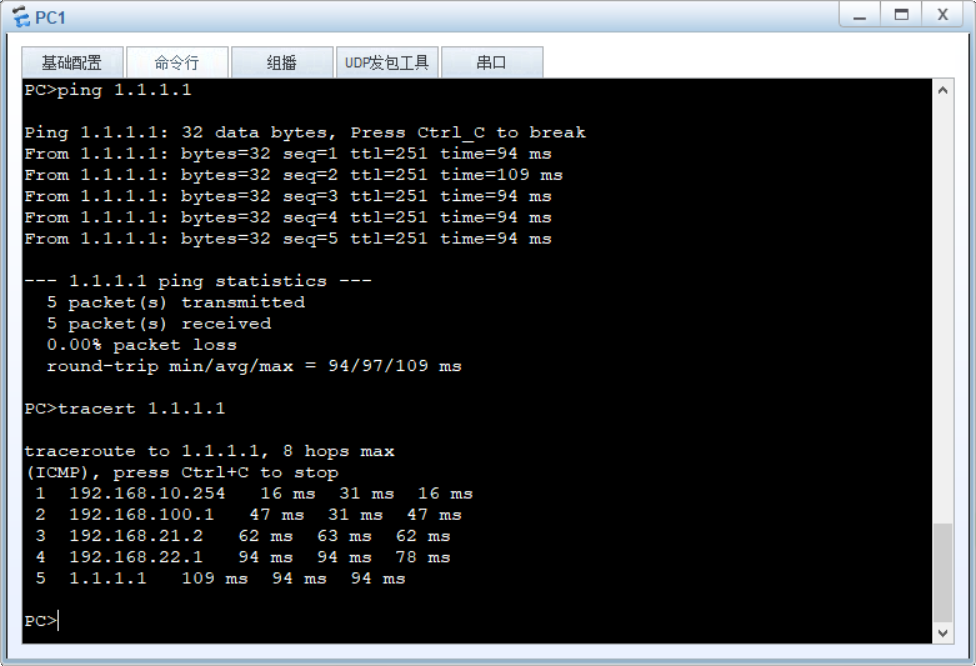
实验拓扑
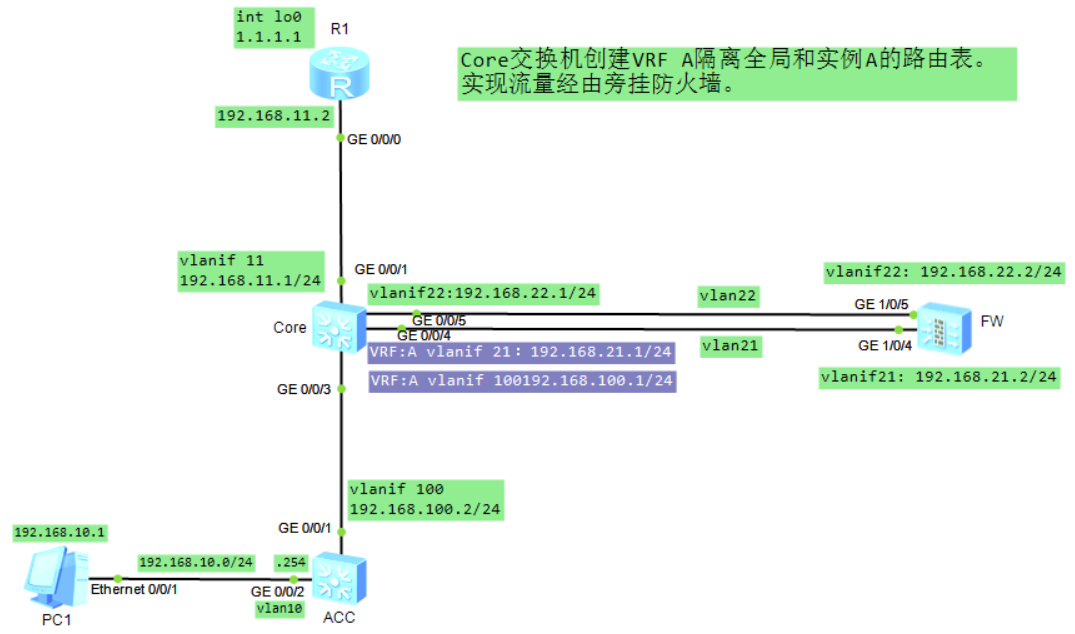
PC1 访问R1,流量由Core交换机的VRF A进入vlan21到达防火墙,防火墙转发到vlan22回到Core交换机后再转发至R1。ACC-CoreVRF-FW-Core-R1开启ospf
配置命令
#ACC设备
sys
sysn ACC
vlan 10
int vlan 10
ip addr 192.168.10.254 24
int g0/0/2
port link-type access
port default vlan 10
vlan 100
int vlan 100
ip addr 192.168.100.2 24
int 0/0/1
port link-type trunk
port trunk allow vlan 100
undo port trunk allow vlan 1
ospf 1 router-id 3.3.3.3
area 0
network 192.168.100.2 0.0.0.0
network 192.168.10.0 0.0.0.255#Core设备
sys
sysn Core
vlan batch 11 21 to 22 100
vlan 100
ip vpn-instance A
route-dist 1:1
int g0/0/3
port link-type trunk
port trunk allow vlan 100
int vlan 100
ip bind vpn-instance A
ip addr 192.168.100.1 24
int g0/0/4
port link-type trunk
port trunk allow vlan 21
int vlan 21
ip bind vpn-instance A
ip addr 192.168.21.1 24
int g0/0/5
port link-type trunk
port trunk allow vlan 22
int vlan 22
ip addr 192.168.22.1 24
ospf 1 router-id 192.168.11.1
area 0
network 192.168.11.1 0.0.0.0
network 192.168.22.1 0.0.0.0
ospf 2 router-id 192.168.21.1 vpn-instance A
area 0
network 192.168.21.1 0.0.0.0
network 192.168.100.1 0.0.0.0#FW设备
sys
sysn FW
icmp ttl-exceeded send
vlan batch 21 to 22
int g1/0/4
portswitch
port link-type trunk
port trunk allow-pass vlan 21
int vlan 21
ip address 192.168.21.2 24
int g1/0/5
portswitch
port link-type trunk
port trunk allow-pass vlan 22
int vlan 22
ip address 192.168.22.2 24
firewall zone trust
add interface Vlanif21
firewall zone untrust
add interface Vlanif22
security-policy
rule name FW_Core
source-zone local
source-zone trust
source-zone untrust
destination-zone local
destination-zone trust
destination-zone untrust
service icmp
action permit
ospf 1 router-id 2.2.2.2
area 0
network 192.168.21.2 0.0.0.0
network 192.168.22.2 0.0.0.0#R1设备
sys
sysn R1
int g0/0/0
ip addr 192.168.11.2 24
int lo0
ip addr 1.1.1.1 32
ospf 1 router-id 1.1.1.1
area 0
network 1.1.1.1 0.0.0.0
network 192.168.11.2 0.0.0.0结果验证